Strong Security Tips To Protect Your Business From Cyber Attacks, Straight Away
The internet has been a trump card for small- and medium-sized businesses. But along with the boons, it also brings the risk of cyber attacks, attempts to steal information or money, or to disrupt your operations. While a multinational corporation typically has the organizational resilience to deal with the devastating effects of a breach, small/medium businesses may not have the resources to respond and recover. So, it's vital to manage these risks and prevent or detect online attacks with basic security practices for your people, processes and IT systems.
By Pallabi Ghatak

Clearly, no business is immune to cyber risks irrespective of their size and industry. In 2014, data breaches( incident exposing confidential or protected information.) have been a burning headline. The 2017 Cyber Security Breaches Survey shows that just under half of all businesses were able to identify at least one cybersecurity attack in the last 12 months.

Small businesses face an average annual cost of $34,604 on cyber-related incidents, and only 52% of small businesses have a strategy around cybersecurity, according to a 2018 report by Hiscox, an insurance provider.
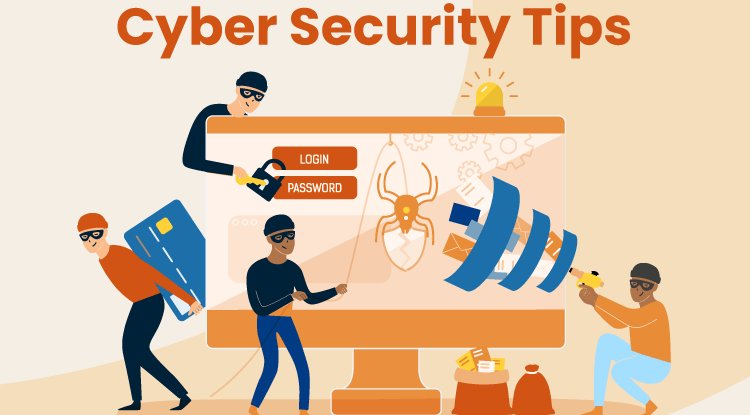
But all businesses can alleviate some of the risks by taking simple steps to protect themselves and their organization online. Here are some strong tips to implement:-

-
KEEP YOUR SOFTWARE UP TO DATE:
Using up-to-date versions of operating systems, applications, firmware, and browser plug-ins helps to protect against the latest threats by patching security vulnerabilities. The sooner these are patched, the lower the risk of your systems being compromised.
-
EDUCATE EMPLOYEES:
National Cyber Security Awareness Month (NCSAM), held every October, raise awareness about the importance of cyber-security. The NCSAM toolkit offers tips and resources to protect against cyber-security threats. The SBA also offers a self-guided online course in cyber-security basics. -
REGULAR CYBER-SECURITY ASSESSMENTS:
It plays a pivotal role in any good security program as it marks the strengths you can augment and the weaknesses you can improve and helps you to discover external and internal risks and assesses all the risks and exposures.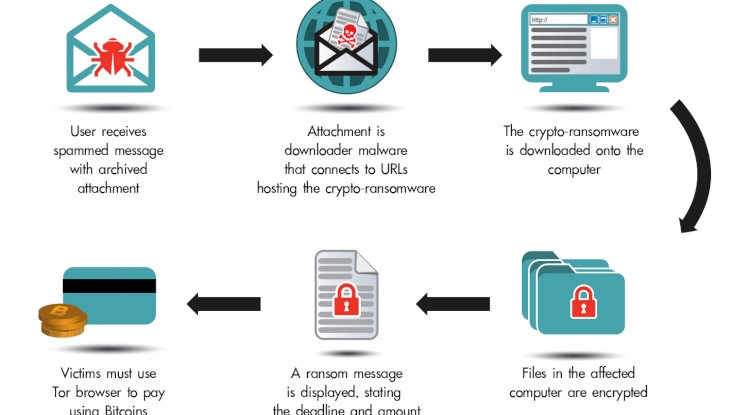
-
USE ROBUST ANTI-MALWARE AND FIREWALL SOFTWARE:
It's important to invest in anti-malware software that has been specially designed to deal with the latest malware threats. While anti-malware software can catch and isolate malware and viruses when they strike, it's critical to prevents these threats from attacking your systems in the first place - and this is where a firewall comes into the picture.
-
STRENGTHEN PASSWORD SECURITY:
Weak, easy-to-guess, or shared passwords are a classic vulnerability. One should use a password manager tool for generating unique passwords and store your log-ins secured, and thus, you never have to worry about writing them down anywhere or forgetting them.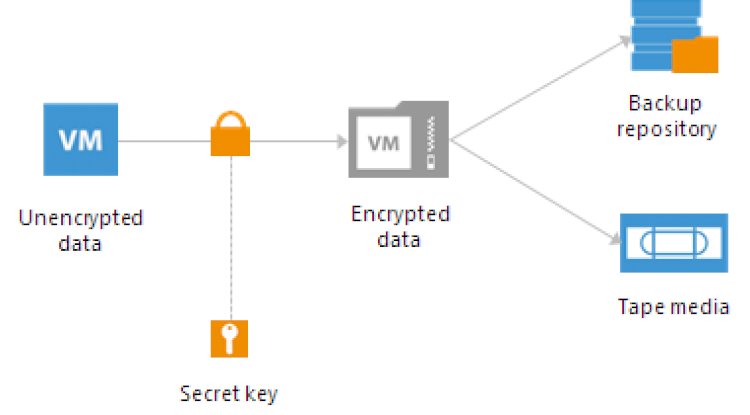
-
ENABLE DATA ENCRYPTION AND PERFORM REGULAR DATA BACKUPS:
Data encryption still remains one of the most efficient forms to tackle against data breaches. If a cybersecurity strategy is effective, it gives a lot of value to data backup and data encryption. Make sure, you first encrypt and then back up sensitive data.
-
THINK TWICE BEFORE DOWNLOADING:
One should be ultra-cautious when downloading and installing software or browser plug-ins. If the software is free, or not from a recognized, trusted software company, it may well include the features of spy on our activity or may install harmful programs. Ideally, your security policy and settings should permit users to install only those programs enables by your system administrator. -
LIMIT AND MANAGE ADMIN PRIVILEGES:
Manage those who do need and don't need admin privileges - limit access to sensitive information and use a strong password to avoid user accounts being compromised. Monitor all activities regularly, in order to detect any unauthorized access attempts.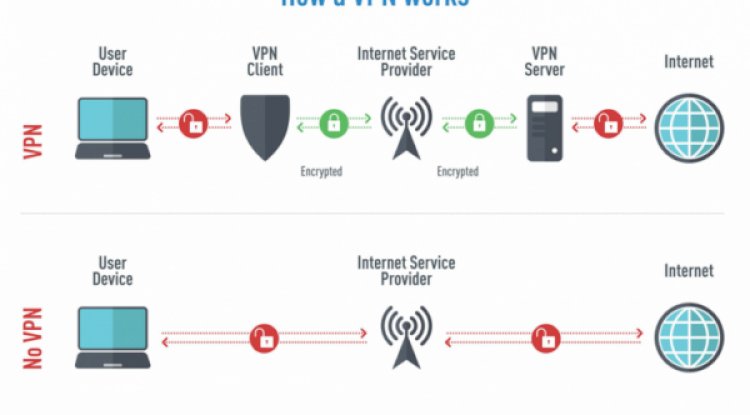
-
GO PRIVATE:
If you are using your systems via public Wi-Fi or any other insecure network, using a virtual private network (VPN) is essential for your business' online security. VPN remain entirely private and enhances security and keeps your data encrypted. You can access your data remotely via a VPN; also it supports you to bypass geo-restricted content and hide your online identity. -
HAVE A DISASTER RECOVERY PLAN:
A well-planned and effective Disaster Recovery Plan will pave the way for a swift reaction if your organization does experience a cyber-attack in the future. It should have a well-defined escalation path, and proactive communication is to be prioritized in case such an unfortunate incident occurs.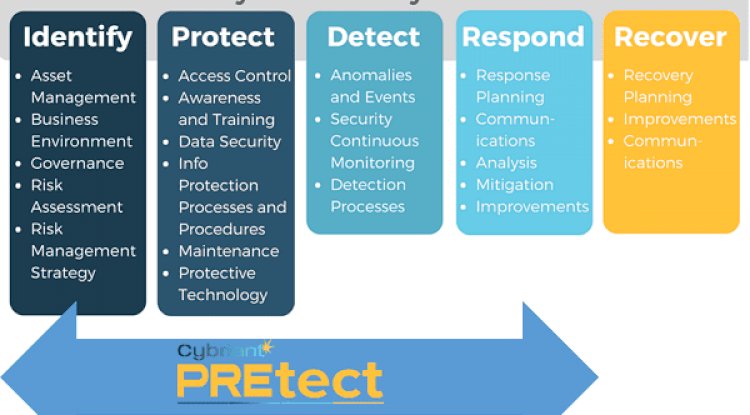
- FOLLOW NIST GUIDELINES: NIST guidelines, especially NIST 800-63B guidelines provide a list of IT guidelines for federal agencies to better manage cyber-security risks.
What's Your Reaction?



















